Configuration of Sitecore 9.x federated authentication with Azure AD
- Sathyamoorthy Srinivasan

- Mar 23, 2024
- 3 min read
Federated authentication enabling users to access sitecore resources through the external providers like Azure AD. Configuration & Implementation of identity provider depends on the provider. Here we are going to see about Azure AD. Here I wrote the small blog to describe the step-by-step implementation.
Let’s start with the provider configuration,
App_Config\Sitecore\Owin.Authentication.IdentityServer\Sitecore.Owin.Authentication.IdentityServer.configor
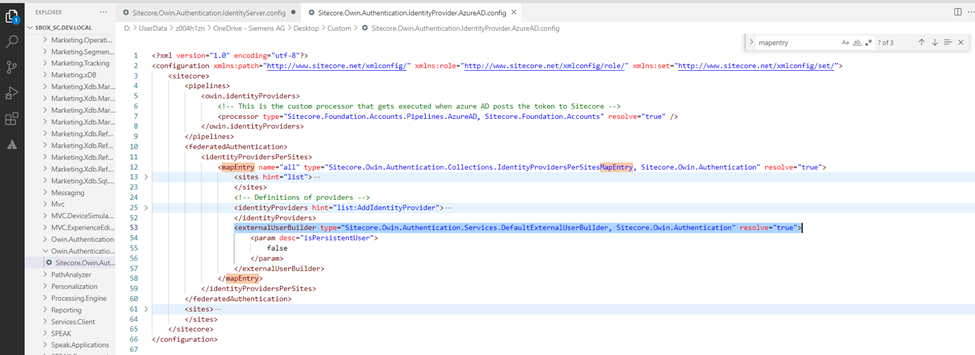
Use a custom config file as shown on the right-side window,

MapEntry nodes to be defined for the authentication scope & by default there would be few nodes predefined already and we can extend them.

Custom processor to the Owin.identityProvides

Patching the pipeline processor as below,

Sitecore has the inbuilt Username generator and we can leverage that feature by adding as below,
Claims & Roles configuration from Identity Providers. Sitecore reads the claims issued for an authenticated user during the external authentication. Also, we can restrict access to the resources to the identities (clients or users) based on their claims.
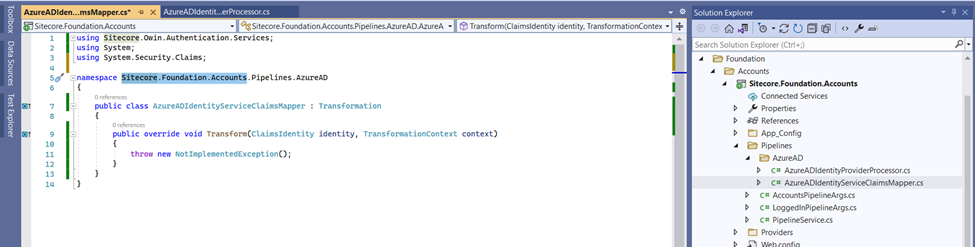
And we can leverage this implementation in the transformation node as below,

Map Properties - If we split the configuration files, we add the name attribute to the map nodes to ensure nodes are unique across all the configs.

Patching the property initializer

Let's hook the User Account from the implementation,
This segment allowing us to share profile data between multiple external accounts and a persistent account detail side by side. If a persisted user claims the roles which has been assigned with them, federated authentication shares these with the external accounts to the requested systems.
On the mentioned below use cases, the connections to an account will be taken care by default in a automated way. And the sitecore signs out the authenticated user, creates a new persistent account, and then authenticates it:
The user is already authenticated on the site.
The user signs in to the same site with an external provider.
There is not already a connection between an external identity and an existing, persistent account. In an implementation Identity, signInManager.ExternalSignIn(...) then returns SignInStatus.Failure.
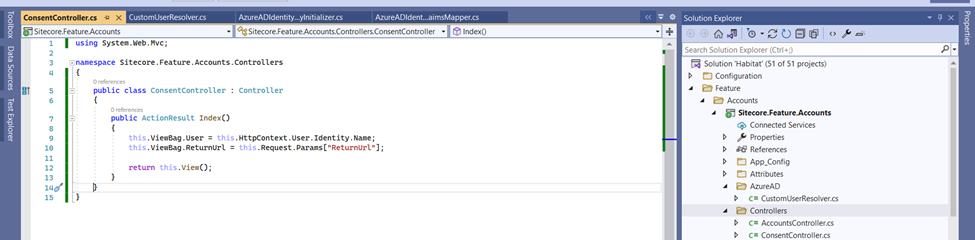
To bind the external identity to an already authenticated account, you must override the Sitecore.Owin.Authentication.Services.UserAttachResolver class using dependency injection as below,

Let's have a controller action method for the front end implementation,
Front end page to render the results
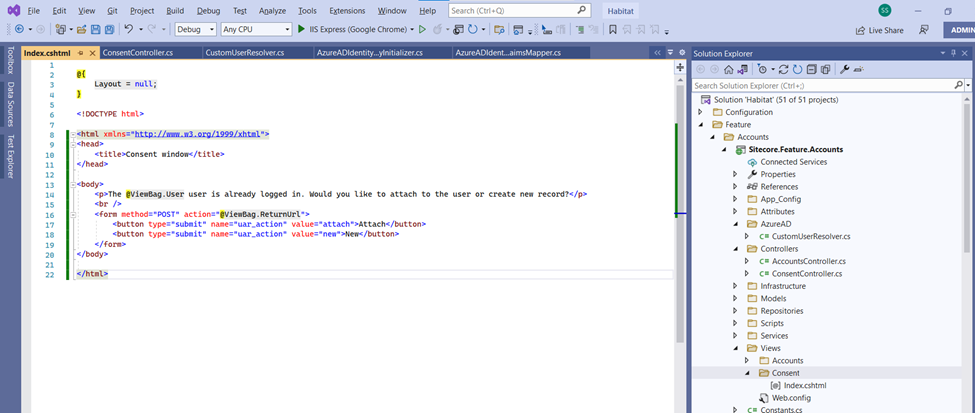
Let's add service configurator to declare the user resolver as Singleton
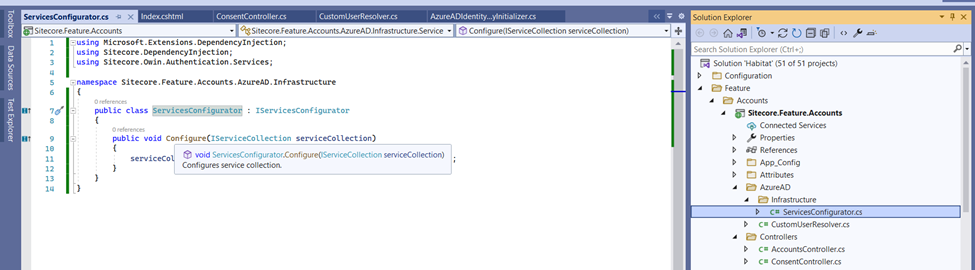
Patching the custom Service configurator to initialize
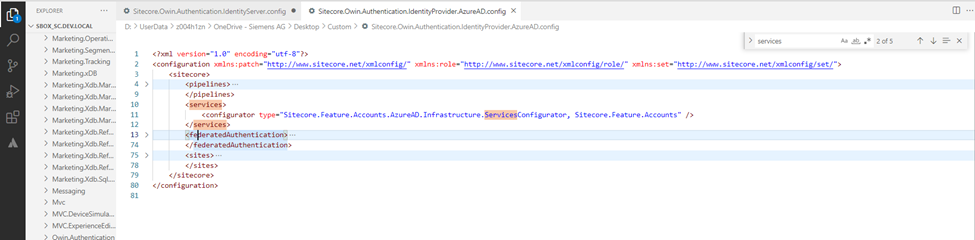
We got the access to the account & the Next thing we need to manage the account connection programmatically. User manager object can be retrieved from Owin Context also the below syntax can be used to perform account detail operations
IOwinContext context = HttpContext.Current.GetOwinContext();
UserManager<ApplicationUser> userManager = context.GetUserManager();
Task<IList<UserLoginInfo>> GetLoginsAsync(ApplicationUser user);
Task<ApplicationUser> FindAsync(UserLoginInfo login);
Task<IdentityResult> AddLoginAsync(ApplicationUser user,UserLoginInfo login);
Task<IdentityResult> RemoveLoginAsync(ApplicationUser user,UserLoginInfo login); Setting up the persistent & virtual users
Virtual Users are when you authenticate users through external providers, Sitecore creates and authenticates the user with proper access rights. there was an issue with this kind of user that, user session data is not persisted across the sessions. Hence, that's the reason we need to have a persisted user for the every authenticated user. When a user uses external authentication, Sitecore creates and persists a new user, and binds this user to the external identity provider and the user ID from that provider. The next time that the user authenticates with the same external provider and the same credentials, Sitecore finds the already created and persisted user and authenticates it.
The identityProvidersPerSites/mapEntry node contains an externalUserBuilder node. which can be overridden as well

<externalUserBuilder type="Sitecore.Foundation.Accounts.Pipelines.AzureAD.AzureADExternalUserBuilder, Sitecore.Owin.Authentication">
<IsPersistentUser>
true
</IsPersistentUser>
</externalUserBuilder>Also, we need to ensure when we implement the user builder, we must not use this to create a user in a database. It must only create an instance of the ApplicationUser class.
Generate the Sign-In Links
There is a pipeline 'getSignInUrlInfo'. This pipeline retrieves a list of sign-in URLs with additional information for each corresponding identity provider in this list.
var args = new GetSignInUrlInfoArgs(site: "sbox_sc", returnUrl: "/");
GetSignInUrlInfoPipeline.Run(corePipelineManager, args); We need to ensure couple of things here,
sign in links should be implemented with POST requests only
Use the Sitecore dependency injection to get an implementation of the BaseCorePipelineManager class.
Happy coding! and keep exploring the new stuff :-) !



Comments